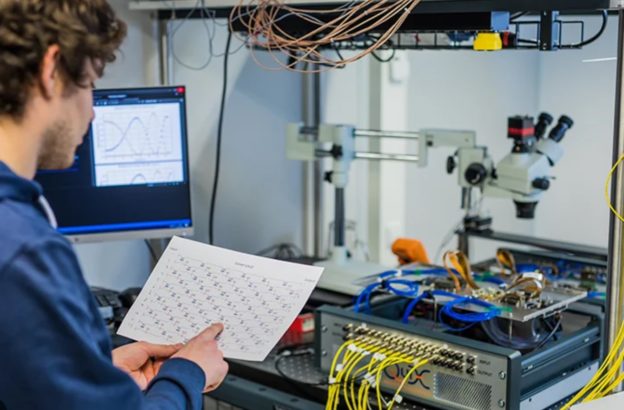
Young Aussie, the Alleged Mastermind Behind Spyware Used by Domestic Violence Thugs
A 24-year-old man from Australia has been found to be the creator of software. This software is used by stalkers and domestic abusers to track and harass their victims. What’s even more surprising, the Aussie from Melbourne developed the Imminent Monitor Remote Access Trojan (RAT) when he was only 15 years.

Young Aussie, the Alleged Mastermind Behind Spyware Used by Domestic Violence Thugs.
Once installed on the victim’s computer, the spyware grants abusive partners and other criminals control over their devices. They can access private files, steal personal information, and even turn on microphones and webcams for spying.
The harmful software sold for just $35. It was advertised on an online hacking forum. Almost 14,500 people from around 128 countries bought it. The Australian Federal Police estimates that tens of thousands of people worldwide become victims of spyware.
In Australia alone, over 200 people purchased the RAT, including PayPal users with a history of domestic violence. Once child sex offenders also popped up on the list. Besides unearthing the spyware users, the AFP also identified 44 Aussies as victims.
According to Christ Goldsmid, the cybercrime boss, one unique aspect of this intrusive software was its cloaked nature.
While cybercrimes might sound like crimes against computers and their networks, that’s far from the truth. These crimes have a significant impact on the real world. For example, the Imminent Monitor’s Remote Access Trojan (RAT) facilitates stalking and domestic violence.
In fact, 13 individuals got arrested, and over 430 devices got seized across the globe.
What’s Next for The Alleged Creator of the Spyware?
The AFP arrested the suspected mastermind. They accused him of creating hacking software. This software has helped domestic violence offenders harm many lives.
On July 6th, a magistrate gave the Australian a summons. He faces six charges for developing, launching, selling, and managing malware from 2013 to 2019.
According to police, the young adult made about $400,000 from the sales of the spyware. Most of which he spent on consumable and disposable items, and food delivery is one of them.
A 42-year-old woman at the Frankston home was also charged in court. She is accused of benefiting from the crime.
How Law Enforcement Agencies Discovered the RAT (Remote Access Trojan)
In 2017, the Australian Police Federation started project Cepheus. They got an alert from the FBI about suspicious remote access malware. This led to an active investigation that involved more than a dozen law enforcement bodies in Europe.
Both private sector and law enforcement agencies (internationally and locally) worked together to handle cybercrime. In 2019, the AFP successfully shut down the software. This stopped it from causing problems for millions of devices around the world. But that’s not the end of it. The investigation into the matter continues.
How Domestic Abusers Use Spyware
Today, domestic violence perpetrators use thousands of apps to secretly monitor their partners. These tools are simple to install, hard to detect, and marketed via a shadowy web of online blogs, adverts, and videos describing how to use them for illegal gains.
They not only include traditional spyware but malware designed for more benevolent uses, including monitoring kids and finding phones. Because of this, it’s impossible to leverage existing anti-spyware tools to shield against them.
Creators of these apps actively promote them to abusers using a webpage titled “Mobile Spy App for Personal Catch Cheating Spouses” or “track my girlfriend.” Sometimes the web pages can contain an image of a man gripping the arm of a lady with scratches on her face.
Google and Apple app stores don’t allow spyware to be sold on their platforms. However, cybercriminals can design spying apps that mimic legitimate software and can be found in Google and Apple. Once downloaded and installed, abusers, can use the apps for illegal purposes like monitoring their victim’s location, conversations, and so on. In most cases, these activities lead to violent or fatal confrontations.

Imminent Monitor RAT diagram
Protecting Yourself Against Spyware
Because spying software often works in the background of devices (invisible to the victims), it’s important to learn how to shield yourself beforehand. Below are a few ways you can block spyware as you browse, clear your email inbox, and beyond.
Use anti-spyware software: An anti-spyware tool or antivirus is your first line of defence against an attacker.
Update your system: It’s always crucial to update your device and browser with the latest security patches to get rid of bugs and fix loopholes.
Pay attention to downloads: Before installing any software or opening any file download online, run them through an antivirus. This way, you can identify and eliminate spyware and malware before they can infect your device.
Avoid Pop-ups: Despite their attractive nature, don’t click pop-ups on your screen. Alternatively, you can install a pop-up blocker.
Final Thoughts
In conclusion, abusers and other cyber criminals are becoming more effective and ruthless at gaining access to their victims’ devices and personal information. Luckily, anti-spyware companies are constantly creating new tools to help shield users. If you or someone you know suffers from domestic violence, call the concerned agencies immediately or visit their official website.
References
- https://www.katherinetimes.com.au/story/7840485/alleged-spyware-creator-identified-as-24yo/
- https://www.boorowanewsonline.com.au/story/7840485/alleged-spyware-creator-identified-as-24yo/
- https://irestmassagechairreviews.com/young-aussie-the-alleged-mastermind-behind-spyware-used-by-domestic-violence-thugs/
- https://www.computerweekly.com/news/252485842/Use-of-spyware-apps-linked-to-domestic-abuse-soars-in-lockdown
- https://cis.cornell.edu/researchers-bring-light-how-spyware-used-domestic-abusers
- https://www.lifewire.com/what-is-spyware-4771730
Written by The Original PC Doctor on 5/9/2022.